Biometrics are likely to influence payment, online identity and access management ecosystems in a way that changes the entire landscape of the digital economy. Because these technologies can identify an individual with great accuracy based on physical and behavioral attributes, they are being used more often for identification and authentication purposes, especially face biometrics.
Face-based authentication, especially 3D face modelling, is in line to play the biggest role in these changes. It will be the subset to watch in the coming years.
The article discusses:
- Global trends in consumer biometrics
- 2D and 3D models for face authentication
- How 2D and 3D face models impact liveness detection
- Considerations for implementing biometric solutions
Trends in consumer biometrics
Consumer biometrics is an emerging market, and it’s promising to be a lucrative one. A 2018 report by Yole highlights four trends that speak to this potential:
- Total value of the consumer biometric market is predicted to grow from $4.8 billion in 2018 to $15.7 billion in 2023.
- In 2013, biometric hardware in high-end cellphones was mainly for fingerprint scanning and was valued at $5 per phone. In 2018, the hardware enabled fingerprint and face- based unlocking and authentication, and was valued at $15 per phone. By 2023, hardware is expected to accommodate fingerprint-, face-, retina- and voice-based biometric components, and be valued at $20 per phone.
- The CAGR for the consumer biometric sensors is expected to reach 20% from 2018 onward. Fingerprint modules are expected to hit 15%, while face-based biometrics are expected to reach 66% CAGR.
- Out of all biometrics, fingerprint/palm are predicted to still be the most used in 2023. 3D facial recognition is predicted to be a close second due to a marginally higher cost.
Biometrics for identification and authentication
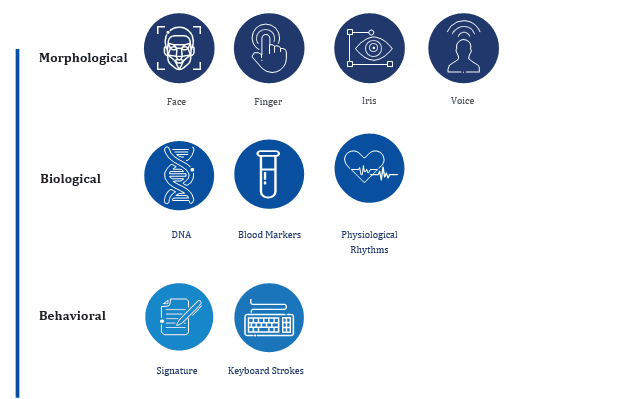
Biometrics-based identification/authentication systems can be broken up into three groups: morphological, biological and behavioral.
The morphological segment drives the consumer biometrics market.
Within this segment, facial recognition
might be the most prominent, because face-based
biometrics enhance our natural ability
to recognize
and distinguish human faces, while being non-intrusive, contactless, and socially accepted.
Identification vs. authentication
Although there is a tendency, especially when referring to face biometrics, to use “identification” and “authentication” interchangeably, the two terms mean different things. Identification refers to the recognition of the user through image-matching.
Authentication operates concurrently, but goes beyond identifying the user to also verify them as a real, live human.
Registration
Real-time liveness detection has become a necessity for authentication systems. Advancements in AI have enabled machines to detect numerous living human traits and characteristics, increasing the accuracy of biometric-based identification and authentication systems.
Similar technology is used for both authentication and identification, but the use cases and implementa- tion details differ subtly. This paper focuses primarily on authentication-based systems, and how they are influenced by 2D and 3D imaging techniques.
Face authentication systems: 2D and 3D face models
Biometric-based face authentication is a complex system. What’s referred to here is a simplified overview of that process.
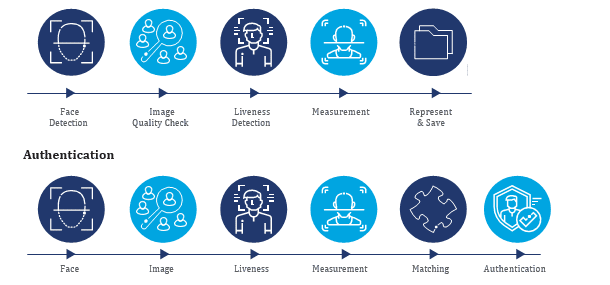
There are two crucial steps in facial authentication process: registration and authentication. The user must register their biometrics (their face) with the system before their face can be authenticated.
Face Registration and Authentication
Face registration and authentication process is depicted in Figure 2. For a detailed note on the process along with influence of 2D & 3D face model in the process and comparison of 2D and 3 D face model from timelessness, various condition at face capture like angle at the time capture, lighting condition etc, please download the detailed whitepaper.
How 3D and 2D face models impact liveness detection
Liveness detection is crucial for maintaining the efficacy of face-based biometric systems. There are many sophisticated spoofing tools—stolen face photos and recorded video; 3D face models capable of blinking, lip movement and other facial expressions; models made of material very similar
to human skin. These tools are not difficult to obtain and can be used to fool face-based biometric systems. Hence, anti-spoofing mechanisms are integrated into biometric systems, and used as prime differentiators in the products/solutions space. There are three main indicators used for liveness detection: motion, texture, and life sign.
To know more about comparative analysis of 2D and 3D face model from motion analysis, texture analysis and life sign detection perspective, please download detailed whitepaper.
How 3D and 2D face models impact liveness detection
Liveness detection is crucial for maintaining the efficacy of face-based biometric systems. There are many sophisticated spoofing tools—stolen face photos and recorded video; 3D face models capable of blinking, lip movement and other facial expressions; models made of material very similar
to human skin. These tools are not difficult to obtain and can be used to fool face-based biometric systems. Hence, anti-spoofing mechanisms are integrated into biometric systems, and used as prime differentiators in the products/solutions space. There are three main indicators used for liveness detection: motion, texture, and life sign.
To know more about comparative analysis of 2D and 3D face model from motion analysis, texture analysis and life sign detection perspective, please download detailed whitepaper.
An important note on security
The First IDentity Online Alliance (FIDO) is an open-industry association working to improve authentication by creating open standards that are more secure than passwords and SMS OTPs, simpler for consumers to use, and easier for service providers to deploy and manage. FIDO, with its members and liaison partners, has become a de facto standard in this space.
In effort to ensure user privacy, FIDO compliance states that biometric data cannot be removed from the devices used to capture it. Additionally, FIDO protocols use standard public key cryptography techniques to provide stronger authentication. At the time of registration with an online service, the client device of the user creates a key pair: one private and one public key. The client device retains the private key and registers the public key with the online service. During authentication, the client device proves possession of the private key to the service by signing a challenge. The private key can be used only after it is unlocked locally on the device by the user. This local unlock can be accomplished by verifying a password, PIN, security key, fingerprint, face or voice biometrics etc.
3D near-infrared cameras in mobile
One of the more accurate ways of creating 3D face models is with an invisible near-infrared (NIR) camera, which eliminates the dependency on ambient light.
The NIR-based facial recognition system works by casting tiny dots on a person’s face. The camera then captures the reflections off those dots, using alternation of reflected pattern and/or time of return to create a 3D image of the person’s face.
The latest smart phones are equipped with NIR-based cameras in the front to allow users to unlock their phones with facial recognition. Face-based biometric authenticator services companies are in the process of getting low-level API so that they can seize the opportunity to provide NIR-enabled 3D facial biometric authentication services in phones. API specifications for manufacturers may vary, making the job of the biometric service provider more complex. EMVCo and the FIDO Alliance have joined hands and are expected to come out with new specification standards for mobile wallet providers and payment application developers to support Consumer Device Cardholder Verification Method (CDCVM). Hopefully, increasing adaptation of FIDO standard will standardize and simplify this ecosystem. Another anticipated benefit of this new specification is additional risk management, leading to a reduction in the number of times a consumer needs to authenticate their face in order to approve payment within the given period.
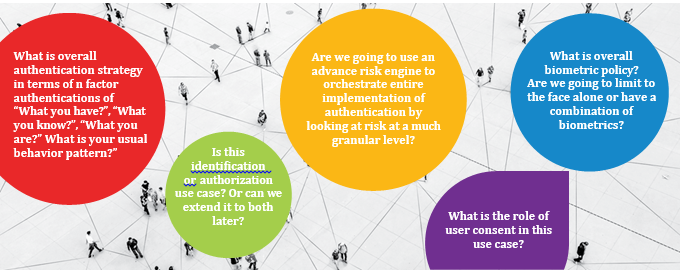
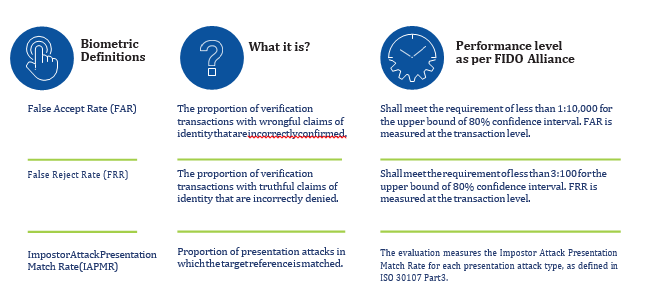
Figure 4: Biometric definitions for acceptance
Considerations for biometrics implementation
The field of computer vision pertaining to face biometrics is moving at a very high speed, and innovations are surfacing that promise greater accuracy in face identification and authentication. With so much in flux, knowing how to choose the right solution for a given situation is critical. The following considerations can help.
The right use case
The proper business case is a basic prerequisite for any successful implementation. One needs to understand the broader picture and consider the questions in Figure 3 before making a final decision about the face-based customer identification and authentication solution.
Answering these questions encourages a holistic point of view, and helps keep implementation on track while preparing for extensions in the future.
Standards and guidelines
There are at least five categories of standards and guidelines that we need to be aware of when choosing a solution in this space: ISO, FIDO, independent third-party testing, applicable country-specific guidelines, and applicable company policy. From an implementation perspective, a well- rounded view of applicable standard guidelines are critical. Here, we focus on one of the critical elements of specification: the biometric definitions for acceptance as shown in Figure 4.
The FIDO alliance provides comprehensive assis- tance to certify biometric components or the entire sub-system. Their Authenticator Certification
Levels are an example of this, providing a framework for security requirements and testing. Indepen- dent third-party testing is the best way to confirm such performance levels, because it harnesses the knowledge of experts in this area.
Closing note
We are experiencing significant technological advancements in the biometric area. The ability to identify and authenticate a digital subject will no longer be a challenge. However, the business use cases for this technology will remain a crucial ethical question, especially if the technology for facial recognition is misused, disregarding personal privacy.
A parallel track of research is currently looking to counter such misuse and to protect privacy. Solutions like lens-shaped masks, face projectors, goggles fitted with LEDs, CV dazzle makeup, and headscarves decorated with faces are being explored as means
to prevent facial recognition from identifying a face correctly. Investments in technology research for biometric identification and authentication need to be balanced by adequate effort to reach a widespread consensus about use of this technology. There needs to be open debate about global policy and standards governing use of biometrics.
References
- “An overview of face liveness detection” from International Journal on Information Theory (IJIT), Vol.3, No.2, April 2014 by Saptarshi Chakraborty and Dhrubajyoti Das
- FingerTec whitepaper on Face Recognition Technology
- https://fidoalliance.org – Various reference are fido alliance site
- “What is a Presentation Attack? And how do we detect it?” by Christoph Busch et. al
- Consumer Biometrics Market & Technologies Trends 2018 report by Yole Development http://www.yole.fr/iso_upload/ News/2018/ PR_BIOMETRICS_CONSUMER_ IndustryOverview_ YOLE_Dec2018.pdf
- Face Image Quality Evaluation for ISO/IEC Standards 19794-5 and 29794-5 by Jitao Sang, Zhen Lei, and Stan Z. Li
- Facing the Future: New Applications and Trends in Facial Recognition — a blog by Anne Corning
- FIDO, EMVCo Prep for Pay-by-Selfie Era – a new article by Tara Seals in infosecurity magazine
- “How Facial Recognition Systems Work” by Kevin Bonsor & Ryan Johnson
- Comparison of 2D/3D Features and Their Adaptive Score Level Fusion for 3D Face Recognition – a whitepaper by Wael Ben Soltana, Di Huang, Mohsen Ardabilian, Liming Chen
- Multi-Modal 2D and 3D Biometrics for Face Recognition a whitepaper by Kyong I. Chang KevinW. Bowyer Patrick J. Flynn
- Source: Consumer Biometrics Market & Technologies Trends report, Yole Développement, 2018 – https://www.slideshare. net/Yole_
- Developpement/consumer-biometrics-market-and- technologies-trends-2018-yole-dveloppement
About the Author
Santanu Dutta
Innovation Engineering Leader for Banking and Financial Services, Wipro
Santanu has 23 years of industry, domain and technology experience in software product and solutions. He is leading an initiative christened as “miliu” – Wipro’s concept bank of future. This initiative conceptualizes the art of possible for a future digital bank and develops innovation accelerators synergizing IPs/solutions of Wipro and its partners.








