Most financial services providers have mandates to use the cloud for business and payment applications. However, migrating to cloud financial hardware security modules (HSMs) has historically seen hurdles such as regulatory compliance, cost concerns, and infrastructural complexity.
Despite these challenges, a financial cloud HSM is a worthy investment for organizations looking to achieve point-to-point encryption and streamline key management processes.
To learn more about the value of cloud financial HSMs in the payments space and what Futurex’s next-generation VirtuCrypt product will bring to the table, PaymentsJournal sat down with Ryan Smith, VP of Global Business Development at Futurex and Tim Sloane, VP of Payments Innovation at Mercator Advisory Group.
What is a hardware security module (HSM)?
The core functionality of a hardware security module revolves around encryption, which Futurex defines as “the process by which data is rendered indecipherable to all except authorized recipients.” Knowledge of encryption helps to decrypt, or convert data into its original form, making it crucial that encrypted data is stored in a secure environment such as a HSM to prevent unauthorized access.
HSMs create and store keys used for encrypted data. Encryption keys, or randomly generated values used to protect secure data, make encryption possible. Similar to a physical key, only those who have the key can unlock (or decrypt) the stored information. HSMs store the information and encrypted keys, and access is granted only to those who use the appropriate key.
Because basic encryption is baked into everything, it may appear that it is very simple. In reality, there are complexities with networks, deploying systems, and managing data in motion and at rest—all of which come with different access requirements. This makes the seemingly simple encryption process extremely complex when moving at scale.
HSMs are key for performance and protection, and go far beyond traditional internet security. In the payments industry, HSMs focus on the cryptography and security of information regarding payment transactions. Banks, transaction processors, card issuers, retailers, and other organizations in the space utilize financial HSMs to ensure that transactions remain secure.
The role of the cloud in financial HSMs
Once a cloud computing environment is in play within an organization’s network, legacy hardware cannot be relied on for adequate security. While five years ago, there was little consensus on what the cloud actually was, it has since become more widely understood as a defined term. Further, many financial services providers are now mandated to use the cloud for business and payment applications. As a result, organizations “are starting to look at how they can take advantage of features that the cloud provides,” explained Smith
“Enterprise workloads are moving to the cloud in vast quantities, and payment applications are no exception,” added Sloane. “As organizations determine the ideal mix of cloud and on-premises technology for their own ecosystem, it’s vital that hardware security modules and encryption key management be included in the conversation.”
Outsourcing encryption by migrating to a cloud financial HSM
Organizations have historically struggled to deploy cloud HSMs, which were largely unable to leave an organization’s premises; much of the difficulty in doing so was related to managing procedures, internal audits, and key management. But as technological advances accelerate, organizations have begun embedding encryption into each of their different applications.
There are also obstacles related to compliance, as organizations must remain compliant even if they decide to outsource their internal network. Comfort level matters too. Organizations have different comfort levels with using the cloud, outsourcing data, and giving up some control over key management.
At the same time, outsourcing encryption to a platform like Futurex’s gives organizations the flexibility to focus on what they want to do, whether that’s processing payments, selling products as a retail, or moving into the healthcare vertical. “Being able to outsource encryption means those resources can now go towards an organization’s core business,” said Smith.
VirtuCrypt cloud financial cloud HSM services
In 2015, Futurex debuted the world’s first financial cloud HSM, putting it years ahead of other organizations in deploying cryptographic solutions for providers of financial technologies. Now, the company is unveiling its next evolution of financial cloud HSMs, which will provide better connection mechanisms to organizations and further remove deployment barriers.
VirtuCrypt is a cloud HSM and key management platform that provides cloud-based access to Futurex’s Hardened Enterprise Security Platform. This platform contains an innovative set of solutions for encryption, key management, tokenization, PKI & certificate authority, data protection, and remote key loading, among other capabilities.
The following chart explores three methods of deployment for Futurex’s cloud HSM. Companies have the option of working with VirtuCrypt Solutions Architects to determine which architecture best fits their needs:
- Hybrid deployment: This approach, released in 2015, is largely used for non-traditional HSM users that want access to the backup redundancy features of HSMs.
- On-premises payment application and financial cloud HSMs: This approach is mainly used by organizations that are new to HSMs. Those that deploy this method have to manage the connection of their applications to VirtuCrypt.
- Fully-hosted cloud option: Asthe next evolution of the cloud payment HSM, this option hosts payment applications in multiple cloud regions to enable full redundancy, high availability, and expansion over time.
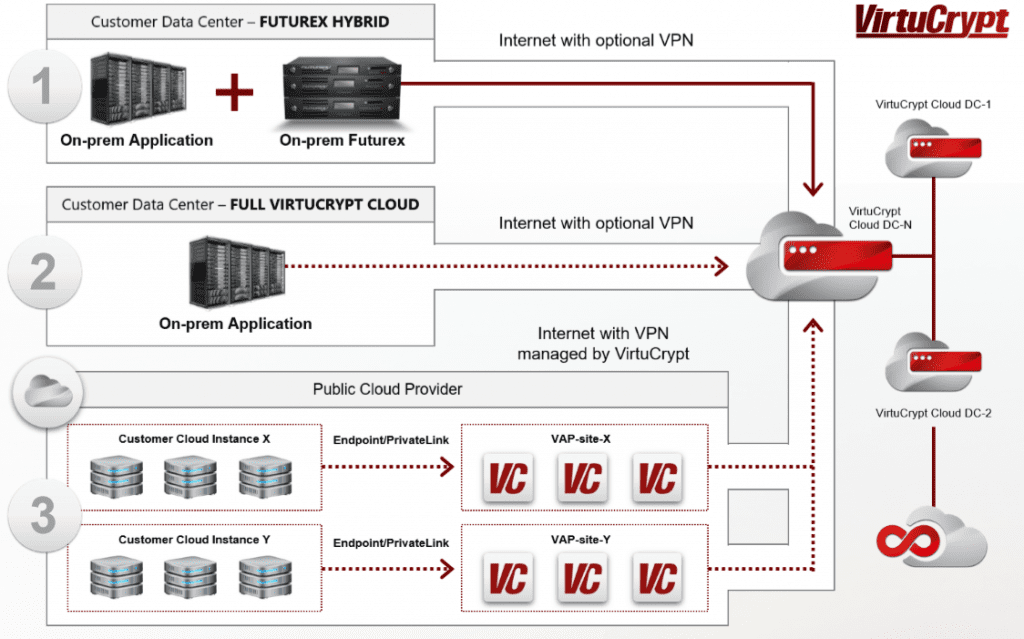
Solutions like Futurex’s help organizations to use financial cloud HSMs to secure data in motion and at rest—while remaining compliant and allowing them to focus on their main business.
For example, Futurex had success working with a major payment manufacturer in 2017. The organization had been providing its own cloud application and performing remote key injection for all of its EMV payment pads, but this was proving to be costly and time-consuming. After migrating to VirtuCrypt, the manufacturer was able to streamline that process and has since directed more efforts to bringing in new technologies and focusing on its primary business.
Conclusion
Cloud financial HSMs are crucial for organizations looking to secure and encrypt data. While there have historically been some challenges in outsourcing encryption to a cloud HSM, it is important for organizations to do so in order to remain compliant and keep important financial data secure. Through its VirtuCrypt products, Futurex can help organizations working in the payments space to migrate to a cloud financial HSM.








